Webpage of Eric Verheul

I am a part-time professor in
the Digital Security Group of the Radboud
University Nijmegen and I am scientifically active in the field of information
security, i.e., the field that deals with the protection of the confidentiality,
integrity and availability of information. I also provide consultancy to
organizations on information security that inspire my research/education and
vice versa.
My inaugural lecture given on Thursday 30
January 2014 in Nijmegen (in Dutch).
Google
Scholar list with citations.
These are some of my papers and
(selected) presentations.
Below I have written some of
my ideas on information security.
The playing field: the increasing challenge of information security
Lack of senior management commitment and awareness
Roughly speaking information security consists of security management
and technical (operational) security. Technical information security deals with
the development of IT security products and surrounding processes that help
organizations to protect their information. Although technical information
security is an important part of information security it needs to be aligned
with security management. Security management is the counterpart of technical
information security and deals with the way management of an organization is
(or rather should be) in control of business information security risks.
Security management is the engine of information security as it drives
information security. A common framework for security management is defined in
the ISO 27001
standard which is based on a continuous Plan-Do-Check-Act cycle. I think
that the alignment of technical information security with security management
is the real challenge in information security: using the right IT security
products to control the real business risks. And that is different from running
all the IT security products the organization’s IT department can think of
without any meaningful involvement from senior management, which is too often
the situation.
To identify the real business risks, thorough risk assessments need to
be conducted.Endnote1
Adequate information security within organizations also requires real
commitment and security awareness of senior management of organizations. And in
my experience senior management of organizations are sometimes naive with
respect to the information security risks of their organizations. And with the
rise of (targeted) attacks, see below, such naivety is getting more and more
dangerous. It seems that senior management of some organizations first
need to have a serious security incident before they act. If the organization
notices the incident at all, that is. Certainly incidents where confidentiality
of information is involved (e.g., privacy, commercial sensitive information,
intellectual property) changes are that organizations do not notice their
occurrence at all.Endnote2
As a mildly amusing anecdote on management awareness; in 2003 I thought
that the so-called vulnerability
exploit in Internet Explorer was a convincing demonstration of the
pitiful state of security in commonly used IT. This exploit implies that any
website has access to the information in a user’s clipboard through Internet
Explorer (the internal memory buffer you fill when you use copy-paste in Word,
Outlook and the like). Just think of the implications: any text you copy and
paste is readable on the internet. That could be passwords, parts of sensitive
emails, privileged stock exchange information enabling trading with prior
knowledge et cetera. And of course by using automatic refreshing web pages, an
attacker could continuously monitor the contents of a user’s clipboard! I
demonstrated the vulnerability to senior management of several organizations
but nobody seemed to be really impressed and I finally gave up. Their response
would typically be that it was a ‘techie’ thing and ‘who could seriously be
interested in my information?’. Baffling. But it explains why security
professionals currently still might have a hard time explaining the seriousness
of possible targeted attacks (see below) at their organization. They might get
the same reaction: ‘it is a “techie” thing’ and ‘who could seriously be
interested in my information?’ Just wait, I guess, and finally you will see who
was interested.Endnote3
The rapidly increasing challenge and the power of money
The trouble is that the challenge of information security is rapidly
getting bigger every day, and security professionals are increasingly lagging
behind on their opponents. This challenge is increasingly getting harder with
the rapid development of:
· security exploits
in ICT and its usage arising from the functionality thirst of users
· the threat of
information from internationally organized crime and intelligence agencies of
hostile nation states in their quest for money and/or power.
If security professionals used to be one step behind, currently they are
two steps behind. One can argue that internal organized crime is gradually
getting the capabilities that were previously limited to intelligence agencies.
With the big difference that organized crime seems to care less when their
activities get exposed. To indicate, due to the organization required for it,
breaking cryptographic keys used to be the prerequisite of intelligence
agencies. But nowadays organized crime also seems organized enough to invest in
breaking keys as is indicated by this Fox-IT
report. I actually worry if perhaps the scientific community, e.g. computer
science students, is unknowingly providing technical assistance to
organized crime. The rise of the involvement of organized crime in cybercrime
therefore also opens a new potential for plausible deniability for intelligence
agencies.
And do not underestimate the power of (tax-less) money. I always like to
play the following game with my colleagues demonstrating the power of money:
“Suppose it’s a Friday afternoon and we have a difficult report
to finish for this important client in New York (i.e. in a time zone -6 hours
from ours) that expects the report today. It’s your girlfriend’s birthday and
you planned this wonderful evening out but I - as the project manager –
am trying to persuade you to keep working on the report all evening and part of
the night too. Would you be persuaded to keep working on the report if I’d
promise you to give you the best job appraisal there is? No, probably not; your
girlfriend would simply not accept that. But what if I promise you 2.000 Euro
in cash if you work the whole evening/night?”
Most of the colleagues I played this game with would be persuaded with
the 2.000 Euro in cash reward; the ones that wouldn’t didn’t have a girlfriend
to start with.
Visible indications of the challenge
There are many visible indications of the increase of the information
security challenge. These indications can for instance be found in the fraud
figures in e-banking published by banks. In the Netherlands this figure was 1.9
million Euro in 2009, 9.8 million Euro in 2010 and 11.2 million Euro in only
the first half of 2011. See NVB
and AD.
Indications can also be found in the rise of attacks from the internet on key persons
(or their secretaries) of organizations whereby they are lured to open email
attachments or to visit certain reliable looking websites. The objective is
deception or – more extreme – retrieval of information by placing espionage
software through the attachment of website. The espionage software effectively
allows the attacker to take over the attacked workstation including its webcam,
microphone and access to fileservers the attacked person has access to. This
perhaps sounds like the script of a bad movie, but this happens and more and
more often too. And of course only a small portion of these attacks is
identified and/or publicized.
One of first publically documented incidents of this type originates
from 2008 with an attack on the Dalai Lama from Chinese soil (Ghostnet)
whereby more than 1200 (!) computers in 103 countries were compromised of which
30% can be considered as high-value diplomatic, political, economic and
military targets. Recently targeted attacks took place in Canada
and Norway.
Moreover the software facilitating taking over computers is getting more and
more user-friendly too as is indicated by the user interface of the SpyEye bot below. SpyEye is one
of the successors of the Zeus bot. In fact, a whole service oriented criminal
industry is emerging where some criminal organizations take care of finding the
vulnerabilities (exploits), others use the exploits in malicious code
(attachments, websites) and couple them with code to be run on the victim’s
machine (payload, typically rootkits) that provide other parties
the services to load bots like Torpig and SpyEye and finally you have people take care of the
configuration of the bots themselves whereby meticulously analysing the website
aimed to harvest from the infection. Depending of the actual attack many more
parties might be involved, e.g. money mules for getting the actual money from
e-banking fraud. And the power of tax-less money keeps the cooperation running
smoothly. Also see this interesting 2009 report on Mebroot / Torpig.
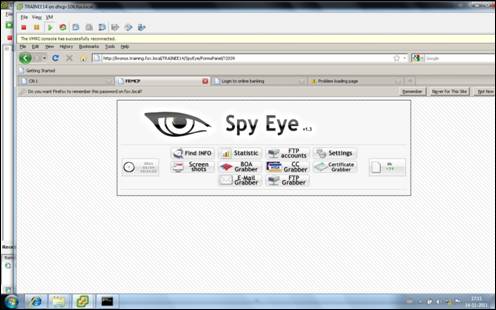
Stepping
stone attacks
Particularly worrisome I think are targeted attacks that take place on
organizations where the objective of the attackers is not access to the
organization itself but access to one of its clients, i.e. the targeted
organizations are only used as stepping stones. An interesting incident of this
type is the targeted attack on EMC/RSA whereby
the cryptographic keys in its SecureID challenge
response tokens were compromised. The attackers (allegedly from Chinese soil)
were interested in getting access to defence contractors such as Lockheed
Martin. Such stepping-stone attacks are particularly worrisome for two reasons:
· organizations are
typically unaware they can be used as a stepping-stone; they are usually have a
hard time finding their own security risk let alone those of their clients,
· there are many
organizations that can be used as stepping stones for getting access to others.
To indicate, any popular website might be an interesting target to allow http
redirect targets to websites infecting them using invisible iframes and
in fact there are already a trading places for compromised websites for
exactly this.
We indeed live in interesting times as security professionals.
My interests in all this
My scientific interests in the field are focussed on security management
(education) and technical information security (research).
I give a course on
security management based on the ISO 27001
standard inspired by the by the challenges I encounter in my consultancy work
implementing security management in practice based on ISO 27001: how to
identify the relevant information security risks an organization faces and how
can senior management be persuaded to act on that? I must admit I have a hard time
explaining the business value of ISO 27001 to technical students that typically
like to solve everything with technical tools instead of with these fuzzy
things called “risk analyses” and “procedures”. The non-conciseness of the ISO
27001 does not help either; standardization institutes still seem to get paid
by the page.
My research is also inspired by my consultancy work and vice versa.
Currently I am focussing on two topics:
· Prevention and
early identification of cybercrime attacks, most notably targeted attacks.
Unchartered territory I think.
· Technical
information security related to compliancy with privacy laws, specifically the
applications of pseudonimization and anonymization
techniques enabling organizations to effectively use (and link) databases with
personal data for analysis purposes or testing purposes. Actually this topic
can be considered as a more positive use of information security, i.e. not to
keep the attackers out, but to enable organizations to do things that were not
possible before.
The added value in both topics consists of a complex technical solution
coupled with a tailored management organization.
You can contact me on one of the email addresses below.
I’m
always amazed by these multinational organizations that seem to think that one
risk assessment and treatment for the whole organization suffices. These assessments
surprisingly often result in the selection of all the 133 controls from ISO 27002 as
risk treatment. When you perform a risk assessment it is also helpful that you
actually know which systems are yours and which are of subcontractors. Once I
was a client site asking whose a particular router was; the client said they
assumed it was owned by their telco and I asked the client to look into this.
Well, it turned out it was not owned by their telco and it actually was
theirs. And of course it was not secured at all, it still had all standard
configuration and passwords active.
As a
mildly amusing anecdote; I once tested the internet Intrusion Detection System
(IDS) of a sensitive organization by running all kinds of automated attacks
against them (e.g. using Metasploit). At a
certain time my network connectivity to the site was lost and I thought that
the IDS had worked. What actually happened was that my Internet Service
Provider had noticed my attempts, decided my connection had been compromised by
a bot and had disconnected my ADSL connection. The organization itself had not
noticed my attempts at all.
· I finally convinced two people to
actively act on the clipboard vulnerability. My wife who started using another
browser and the security officer of a police organization that had its content
scanner configured to remove the ‘getData’ method on
the fly.
· Microsoft actually issued a security
patch related to the vulnerability in 2002. However, apparently they
actually did not consider it a vulnerability that any website could read the
clipboard contents. The vulnerability they addressed was a flaw in the
configuration the concerned user could use to stop this default behaviour
(‘Allow paste operations via script’). Or in the words of Microsoft: “This is
an information disclosure vulnerability. Specifically, it could enable a web
site to programmatically read the contents of a user's clipboard, even when the
user has enabled the setting to prevent sites from being able to do this. The
default setting for this option is to allow programmatic access to the
clipboard. Therefore, the risk created by this vulnerability is no worse than
the default setting for this feature. However, because it allows a security setting
that controls the privacy of information to be bypassed, it does constitute a
vulnerability.”
· The vulnerability (or feature in the
perspective of Microsoft) was active until Internet Explorer 6. Starting from
Internet Explorer 7 the user was warned for a website requesting access to the
clipboard. This is still the behaviour Internet Explorer 8 as you can see here.
I wonder how many people will give act correctly on the request.